A VPN (Virtual Private Network) can be useful in many situations, including:
1. Protecting online privacy and preventing tracking by hiding the user's online activity and IP address from third parties. If you want to check your own IP address, look here.
2. Enhancing online security by encrypting internet traffic and protecting against cyber threats such as hacking, phishing, and malware. For more info, have a look about common cyber threats at one of the branches of the Australian Government : The Australian Cyber Security Centre (ACSC).
3. Bypassing online censorship and geo-restrictions by allowing the user to access content and websites that may be blocked in their location. Geo-blocking can be very annoying in some cases. Learn more about geo-blocking on the well-known anti-virus Avast page.
4. Accessing public Wi-Fi securely by encrypting the user's traffic and protecting against potential security threats on unsecured networks. Encryption is detailed is here.
5. Working remotely and accessing company resources securely by establishing a private connection to a company's network.
In summary, a VPN (Virtual Private Network) is a powerful tool that provides privacy, security, freedom and anonymity when accessing the internet. It does this by encrypting the user's internet traffic and routing it through a private server, hiding the user's IP address and physical location from websites and internet service providers.
Here are some of the best VPNs available in the market, popular and well-reviewed services that might suit your needs.
Each VPN service offers different features and pricing plans, so it is essential to research and compare them before choosing the one that suits your needs. Additionally, you can also check for other independent reviews and user experiences (forum for ex.) to help you make a more informed decision.
There are many well-reviewed VPN services available in the market. Here are some of the top-rated VPN services, based on expert reviews and user feedback:
1. ExpressVPN
Known for its fast and reliable service with a large server network across many countries.
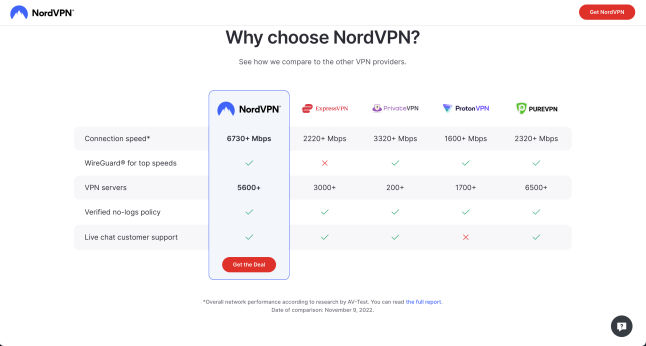
2. NordVPN
Offers strong security features, including Double VPN and CyberSec, as well as a wide selection of servers.
3. Surfshark
Offers unlimited simultaneous connections, a strict no-logs policy, and a user-friendly app.
4. CyberGhost
Known for its easy-to-use app and extensive server network, with over 7,000 servers in more than 90 countries.
5. Private Internet Access (PIA)
Offers advanced security features, such as ad and malware blocking, and a strict no-logs policy.
6. ProtonVPN
Offers high-end security features, including Secure Core servers and Perfect Forward Secrecy, and a user-friendly app.
7. Hotspot Shield
Offers fast speeds and strong security features, including a free version with limited features and bandwidth.
8. IPVanish
Offers fast and reliable service with a focus on security, including a strict no-logs policy.
9. VyprVPN
Offers strong security features, including Chameleon protocol to bypass restrictions, and a proprietary server network.
10. TunnelBear
Known for its easy-to-use app and playful design, as well as a free version with limited features and data.
Advice
It is important to note that each VPN service has its own strengths and weaknesses, and what works best for one person may not necessarily work for another. It's always a good idea to research and compare different VPN services before choosing one that suits your needs.
Here is a comparison of these popular VPN services and their pricing plans (prices are in USD and subject to change):
VPN Service Monthly Plan Annual Plan Biennial Plan Free Trial
ExpressVPN $12.95/month $8.32/month $6.67/month 30-day money-back guarantee
NordVPN $11.95/month $4.92/month $3.71/month 30-day money-back guarantee
Surfshark $12.95/month $4.98/month $2.49/month 30-day money-back guarantee
CyberGhost $12.99/month $3.99/month $2.25/month 45-day money-back guarantee
Private Internet Access (PIA) $9.95/month $3.33/month $2.69/month 30-day money-back guarantee
ProtonVPN $10/month $5/month $3.29/month 30-day money-back guarantee
Hotspot Shield $7.99/month $2.99/month (3-year plan) $7.99/month $2.99/month (3-year plan) 7-day free trial
IPVanish $10.99/month $3.75/month N/A 30-day money-back guarantee
VyprVPN $12.95/month $3.75/month $2.50/month 30-day money-back guarantee
TunnelBear $9.99/month $4.99/month N/A Free version with limited data
Good to note that the pricing plans offered by VPN services may vary depending on factors such as the length of the subscription, the number of devices supported, and the availability of special deals or discounts. Additionally, some VPN services may offer additional features or benefits that are not reflected in this comparison table. Therefore, it's always a good idea to research and compare different VPN services before choosing one that suits your needs and budget.
TOR PROJECT:
The Tor Project is a non-profit organization that develops and maintains the Tor network, a free and open-source software that enables anonymous communication over the internet. Tor stands for "The Onion Router," and it works by routing internet traffic through a network of volunteer-run servers, called nodes or relays, that are spread across the world.
When a user accesses the internet through the Tor network, their internet traffic is encrypted and routed through several relays before reaching its final destination. Each relay removes a layer of encryption, like peeling off layers of an onion, hence the name "onion router." This process makes it difficult for anyone to trace the user's internet activity back to their physical location or identity.
The Tor network is designed to protect user privacy and security, particularly in situations where anonymity is important, such as political activism, journalism, or personal safety. However, it's important to note that using Tor does not guarantee complete anonymity, as there are ways to circumvent Tor's security measures and identify users.
The Tor Project also develops and maintains other tools and services that promote online privacy and security, such as the Tor Browser, a modified version of Firefox that allows users to access the internet through the Tor network, and the Tor Messenger, an encrypted instant messaging client. The Tor Project receives funding from donations and grants and is supported by a community of volunteers who contribute to the development and maintenance of the Tor network and its associated tools.
FOR TECHIES:
You can administrate several tools and configure them in order to protect yourself while browsing online. But that's not an easy game and you have to know what you're doing...
Here are some popular network security tools used to protect against various cyber threats:
1. Firewalls: Firewalls are network security tools that control and monitor incoming and outgoing network traffic. They can be either hardware or software-based and are used to prevent unauthorized access to a network. Several very good firewalls are available here : Iospark, Cisco ASA, Fortinet FortiGate, pfSense, SonicWall, Check Point and Juniper Networks SRX.
2. Intrusion Detection and Prevention Systems (IDPS): IDPS are software and hardware systems that detect and prevent unauthorized access to a network. They monitor network traffic and can detect suspicious activity, such as attempts to exploit vulnerabilities or unauthorized access. More info about IDPS here.
3. Antivirus and Anti-Malware Software: Antivirus and anti-malware software are used to protect against malicious software, such as viruses, worms, and Trojans. They scan files and programs for known threats and can block or remove them. Have a look at our best antivirus and anti-malware software page here.
4. Network Access Control (NAC): NAC is a security technology that enforces security policies for devices accessing a network. It ensures that devices connecting to the network meet certain security requirements, such as having up-to-date antivirus software or being patched with the latest security updates.
5. Web Application Firewalls (WAF): WAFs are designed to protect web applications from cyber threats such as SQL injection, cross-site scripting, and other attacks that exploit vulnerabilities in web applications. Learn more about SQL injection here on the official W3schools website or on Portswigger portal.
6. And of course a VPN...
These are few examples of network security tools. Depending on the organization's security needs, there may be additional tools and measures in place to protect against specific threats.